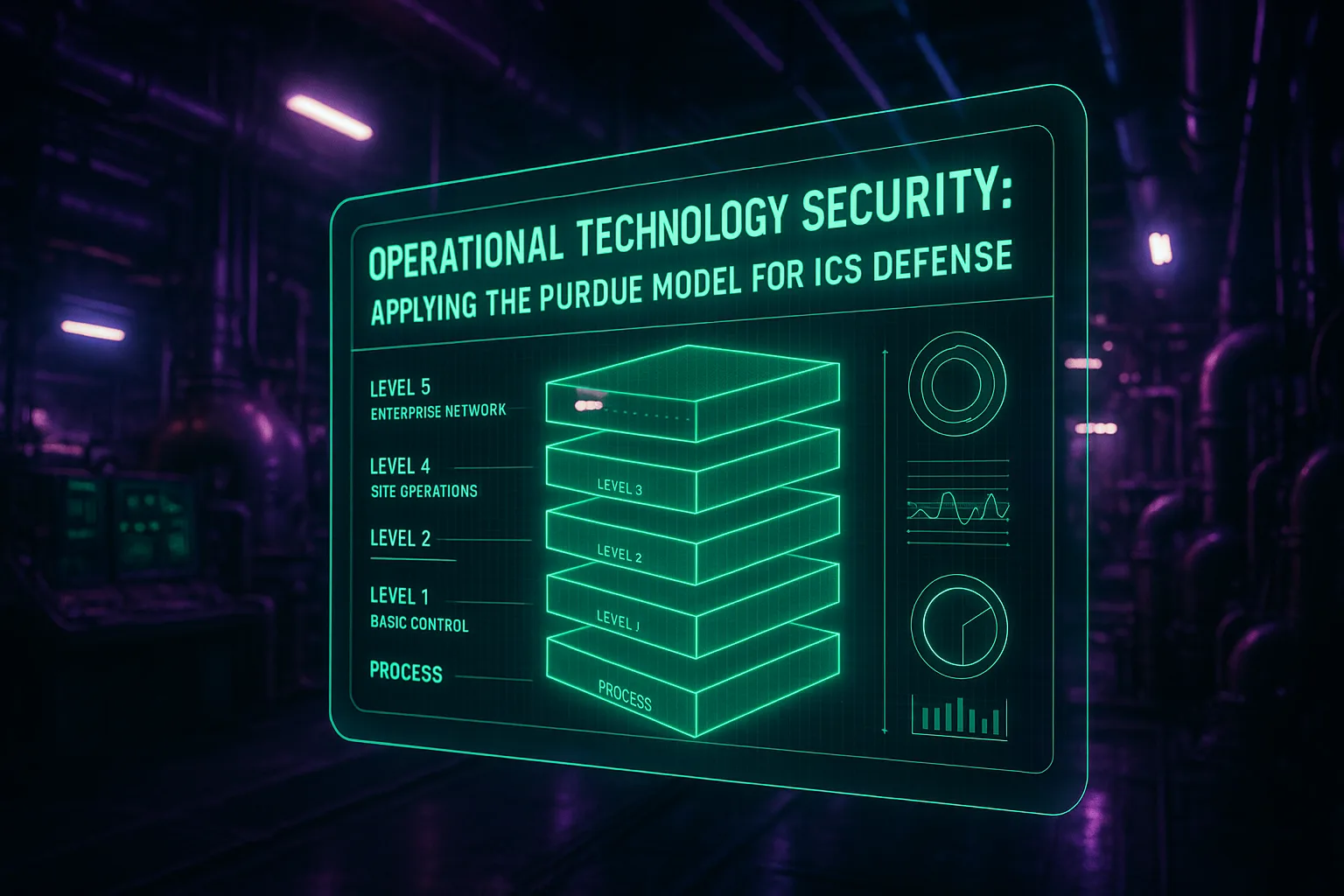
Smart Toy Security: Protecting Your Kids from the Hidden Risks of Connected Playthings
A recent study from a leading consumer rights group was alarming. It found that seven out of ten popular smart toys had significant security vulnerabilities. This isn't just a technical…